Encryption and decryption are a vital part of Adobe Campaign as the campaign application has to deal with a lot of data.
If your implementation needs a data load activity with decryption functionality in it, then this use-case will be of great help. I will take an example of a fully on-premise customer implementation. In this case, the campaign instance is hosted on the client’s infrastructure.
The agenda for this article is as follows:
- Getting a client PGP encryption key
- Receiving an encrypted data file from a client in an Adobe hosted environment
- Decrypting the file for data loading in a workflow
Now for those we are wondering what is the PGP that I mentioned above, let me explain that first.
Pretty Good Privacy (PGP) is a data encryption and decryption utility that provides cryptographic privacy and authentication for data communication. PGP is often used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications. PGP automatically handles file compression and is not necessary to ZIP the file before encryption. Read more
Gnu Privacy Guard (GPG) is the utility that is used to encrypt and decrypt files for FTP. Read more
Client SFTP Site configuration
- You need to create a new SFTP for your instance.
- Your infrastructure team will create and install the GPG Key.
Note:
If the client will be uploading encrypted files, their infrastructure team will provide the public key for encryption and install the private key on the server
Example: The client uses the public key to encrypt the file and upload it on the campaign sever.
If the client will be downloading files, then the client must provide the public key used for encryption, and protect their own private key for decryption.
Example: The client uses the private key to decrypt the file place on the campaign SFTP.
3. Perform the SFTP white-listing for the instance.
Client PGP Key configuration
- Build a
test file with the public key and push it to the hosted environment. - Verify whether the
test file is received in the host environment. - Verify that the file will decrypt with the private key via the data loading activity of a test workflow. See below for instructions on creating the workflow.
- If the client will be downloading files, build a workflow to create a
test file in the environment and encrypt it. Ensure that the customer can download and decrypt the file.
Configure the Workflow to Decrypt an Incoming File
Here you are loading the data from an encrypted csv file place on the SFTP.
In the Data Loading activity:
- Configure the file format section as needed.
- Set ‘Pre-process the file’ radio button.
- Set Command to:
gpg --decrypt FilePathWithFileName
…HostFilePath
This path and name may be passed as variable via a script or a File Collector activity, or the name may be computed from the date or any other agreed-upon naming convention.
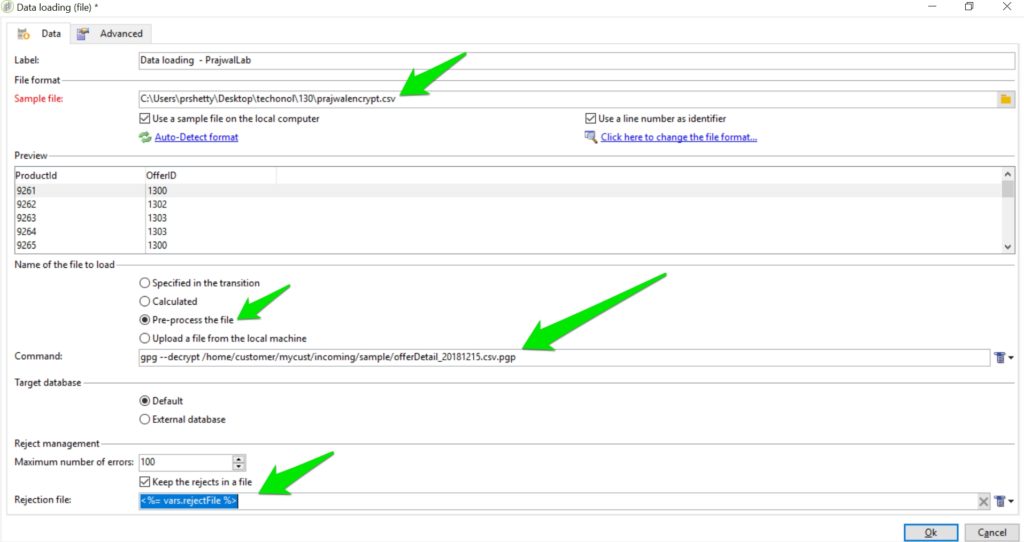
This will decrypt the file in place, removing the .pgp suffix.
Hope this helps.
